
Image: iStock/OrnRin
Phishing attacks seem like a relatively simple tactic on the part of cybercriminals. Set up a phishing webpage, create your phishing email, send the email to targeted recipients, and then wait for those stolen account credentials and other compromised information to come your way.
On the receiving end, a successful phishing campaign can damage an organization in more ways than one. A report released Sunday by security provider Proofpoint looks at the impact of a phishing attack and offers tips on how to combat one.
For its “2021 State of the Phish report,” Proofpoint collated data from several sources:
- A third-party survey of 3,500 working adults in the US, UK, Australia, France, Germany, Japan, and Spain;
- a third-party survey of 600 IT professionals across the same countries;
- more than 60 million simulated phishing attacks deployed by Proofpoint customers for internal training; and
- more than 15 million phishing emails reported by end users.
2020 saw a slight increase in phishing attacks among Proofpoint customers. Some 57% said their organization was hit by a successful attack last year, up from 55% in 2019. More than 75% of the respondents said they faced broad-based phishing attacks–both successful and unsuccessful–in 2020. Using such an approach, cybercriminals cast a less targeted but wider net in hopes of compromising as many people as possible.
SEE: Social engineering: A cheat sheet for business professionals (free PDF) (TechRepublic)
However, more targeted campaigns also posed a threat last year. Among the respondents, 66% saw more targeted phishing attacks last year, while 65% were hit by more Business Email Compromise (BEC) attempts.
Targeted attacks reach fewer people but are more focused and sophisticated and less likely to get caught by security defenses. By researching specific people or roles within an organization, cybercriminals can deploy spearphishing attacks and BEC campaigns as well as whaling attacks, which target CEOs or other high-ranking individuals.
A successful phishing attack can impact an organization in several ways. Data loss was the greatest side effect, cited by an average of 60% among those surveyed. Compromised accounts or credentials was the second biggest effect, mentioned by 52% of the respondents. Additional outcomes from a phishing attack included ransomware infections as cited by 47%, other malware infections by 29%, and financial loss or wire transfer fraud by 18%.
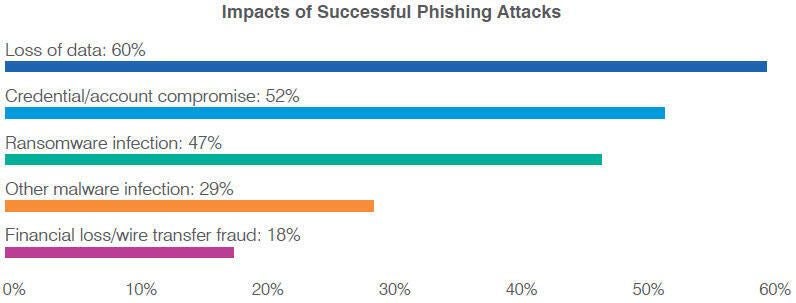
Image: Proofpoint
Beyond email-based phishing attacks, cybercriminals like to employ other tactics. Some use social media, some use text messaging, and some use voicemail. Last year, 61% of those surveyed were hit by social media attacks, 61% by smishing (SMS phishing) attacks, and 54% by vishing (voice phishing) attacks.
Of course, the coronavirus pandemic created fodder for phishing attacks. Millions of pandemic-related emails were blocked by Proofpoint alone last year. Though the number of such attacks has dropped since peaking in April and March of 2020, criminals continue to exploit the virus by focusing on more recent events such as stimulus funding and the vaccine rollout.
The simulated phishing emails sent to employees by their organization used such themes as “Singapore Specialist: Coronavirus Safety Measures,” “COVID-19 Hospital Visit,” “FBI Warning!!! Coronavirus Scams,” and “COVID-19 Infected Our Staff.” In some cases, the failure rate approached 100%, meaning almost all of the employees failed to detect these as phishing scams. For more frequently-used COVID-related templates, failure rates were much lower, ranging from less than 1% to just over 20%.
To help your organization and your employees thwart phishing campaigns, Proofpoint offers a variety of suggestions:
Elevate users to stakeholder status
- Don’t assume users understand cybersecurity lingo. If they don’t recognize the terminology you use, you risk a disconnect from the start.
- Make it personal for users. Cybersecurity isn’t just a “work thing,” and users should understand that. Help them see the overall value of improving their security savvy–at work and at home.
- Be clear about expectations and communicate regularly with users. They should know about the goals of your program and planned activities. Obviously, this does not apply to the exact timing of phishing tests.
- Make users feel empowered. They are often the only thing standing between an attacker’s success or failure. Give your users the tools they need and teach them how to use them.
- Give users a safe space to learn, make mistakes, practice, and learn some more. If you feel you must use a consequence model, first give employees the opportunity to learn how to avoid the behaviors for which they might be punished.
- Explain how better behavior by employees improves the organization’s security. In most cases, negatives are usually already clear, and there’s a focus on what users are doing wrong rather than what they are doing right. Flip the conversation and give users the opportunity to focus on the constructive aspects of learning about cybersecurity. They should clearly know what you are looking for from them and why you are asking them to make security a priority.
Keep benchmark data in perspective
Benchmark datapoints about average failure and reporting rates are helpful from a comparative perspective. If you’re lagging behind the averages, that doesn’t mean your organization is “failing.” By the same token, if you’re ahead, that doesn’t mean you can ease off.
Marry threat intelligence and security awareness training
Almost all the organizations surveyed for the report use threat intelligence to inform their training decisions–there is room for improvement. To take advantage of threat intelligence, organizations should train users on topics that relate to known attacks on the organization, create phishing tests that mimic trending threats, and deliver specific training to people who are being targeted by certain types of attacks.
Correlate awareness and training activities with other security functions
Security awareness training programs often work independently of other security programs. Ideally, all user-related security functions should intersect and inform. Consider linking password training to metrics such as the number of password reset requests or the number of times it takes a user to create a new password when prompted. Look into tracking data loss prevention violations alongside data security training activities.
Such efforts can create a more results-oriented approach to security, show users how their behavior has an impact on security, and provide your CISO with measurable and actionable data about your team’s effects on your organization’s overall security posture.