
Microsoft
SecurityHow to install the OpenSSH server on Windows with PowerShell
If you've ever had a need to SSH into a Windows machine, Jack Wallen shows you how to make that possible with the help of PowerShell.

If you've ever had a need to SSH into a Windows machine, Jack Wallen shows you how to make that possible with the help of PowerShell.

Sometimes you just need a quick means of converting a spreadsheet to a comma-separated values file. When you don't have a GUI to take care of the task, Jack Wallen has the perfect command for the job.

Data intelligence is a way to integrate data to help companies make better decisions. Tom Merritt can tell you all about it.

Only 25% of consumers surveyed by NTT Application Security said they'd take their online business elsewhere following a data breach.

If Multipass is your virtual machine environment of choice, and you wish you could add a GUI to your VMs, wish no more. Jack Wallen shows you how to do just that.

OpenAI defends its shift to a for-profit model, citing funding needs and mission alignment, as Musk’s lawsuit threatens its future ahead of a 2026 trial.

VPNs are popular due to the fact they add security and privacy to what are otherwise fairly open Wi-Fi and public internet channels. But can VPNs be tracked by the police?

A tech analyst warns that an iPhone could cost up to $3,500 if made in the USA.




In this episode of Top 5, we dive deep into the exciting features, updates, and enhancements that Zoho People will offer in 2024.

Proofpoint threat intelligence continues to demonstrate attackers’ focus on end users, and it validates the need to take a people-centric approach to cyber security. But what if organisations aren’t following that model? In this section of the report, you’ll find the results of our five-question, seven-country survey, which was designed to gauge the fundamental cyber ...

Proofpoint threat intelligence continues to demonstrate attackers’ focus on end users, and it validates the need to take a people-centric approach to cyber security. But what if organisations aren’t following that model? In this section of the report, you’ll find the results of our five-question, seven-country survey, which was designed to gauge the fundamental cyber ...

What’s on the chief data and analytics officer’s agenda? Defining and driving the data and analytics strategy for the entire organisation. Ensuring information reliability. Empowering data-driven decisions across all lines of business. Wringing every last bit of value out of the data. And that’s just Monday. The challenges are many, but so are the opportunities. ...

Analytics is a critical part of most organisations operational models. No matter what industry you’re in, moving quickly from data and analysis to tangible results provides competitive differentiation. At least that’s what many vendors promise. But in today’s crowded analytics marketplace, who can you trust? What’s needed to deliver on the promise of transforming data ...

More than 80 percent of interview subjects say analytics has reached the boardroom in their organisations, while just 35 percent say analytics are deployed at an enterprise scale. These two results indicate that even though most executives have bought into the use of analytics at a strategic level, the deployment of a full analytics strategy ...

Creating a more diverse workforce can have many benefits for tech companies. Tom Merritt shares five tips for getting women interested in applying.
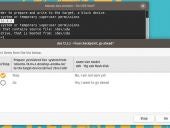
Having a version of desktop Linux on a USB drive isn't of much use unless you can store files to it. Jack Wallen shows you how to create such an instance with mkusb.
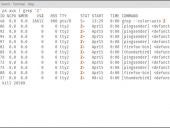
Zombied processes can indicate a problem with a piece of software. Jack Wallen shows you how to find and kill those zombies on your Linux data center servers.
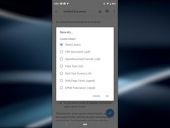
If you need a word process for your Android device, Jack Wallen says you cannot go wrong with one of these five.

Your nmap service probe database is probably way out of date. Jack Wallen shows you how to update that special file to the latest version.



















